Only in Punjab, where AAP volunteers have guarded the EVMs round the
clock, Amit Shah could not tamper with the results and therefore AAP
has won 4 seats there and Jaitley has lost, reflecting the real national mood.
Videos and Images
Images (click to enlarge)
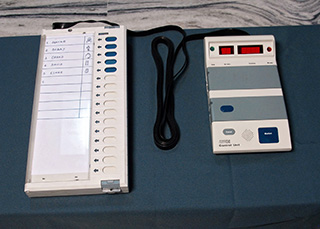 |
Indian EVMs consist of a ballot unit (left) used by voters and a control unit (right) operated by poll workers. |
 |
The control unit displays vote totals for each candidate at the end of the election. |
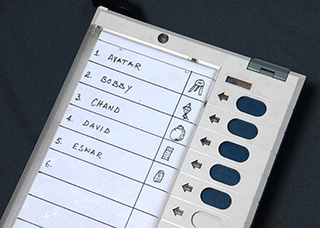 |
The ballot unit is used by voters, who simply press the button corresponding to the candidate of their choice. |
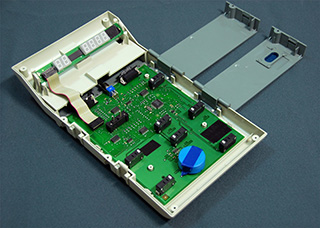 |
Inside the EVM is a main circuit board with the CPU
and vote memory, as well as a smaller display board. This hardware has
never before been subjected to detailed public scrutiny. |
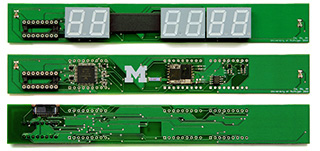 |
We demonstrate how criminals could replace the
display in the EVM with a dishonest look-alike, shown here. We added
parts, hidden under the LEDs, that substitute dishonest vote totals when
showing election results. |
 |
We developed an application that runs on an Android
mobile phone and wirelessly tells the dishonest display which candidate
should receive the stolen votes. |
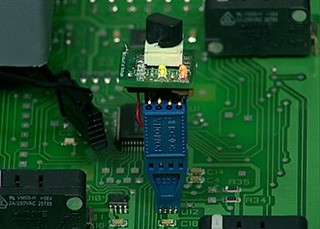 |
We also developed a demonstration attack device that clips on to the memory chips inside the EVM and steals votes. |
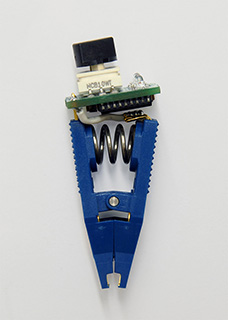 |
The clip-on attack device is small enough to fit in a shirt pocket. |
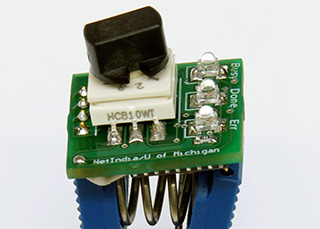 |
Close-up of clip-on vote stealing attack device. A rotary switch allows the attacker to select which candidate to favor. |
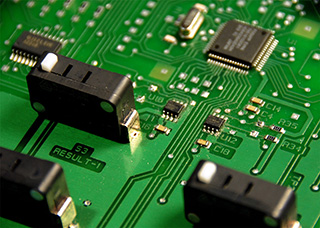 |
The processor in the EVM (upper right) is
designed so that the election software is hard to read out. Election
officials claim this is a security feature, but it makes it difficult
for even the authorities to verify that the correct software is in the
EVMs. |
 |
Frames from an official poll worker instruction video show how the control unit is sealed with red wax and string (top). The seals protecting the screw holes on the case consist of printed paper stickers (bottom). Such low-tech seals could be easily faked and provide an extremely weak defense. |
 |
EVM report authors (left to right) J. Alex Halderman, Hari K. Prasad, and Rop Gonggrijp, holding the EVM they studied. |
 |
A comic about EVMs featured in our video. |
Videos
|
India's EVMs are Vulnerable to Fraud
Our explanatory video (transcript). A broadcast quality version is available upon request. Please email authors@IndiaEVM.org to enquire.
|
|
Un-cut attack footage
This video shows the dishonest display attack as a single take, without
any editing or splicing. The entire demonstration takes about ten
minutes, most of which is spent waiting for the EVM.
|

The videos and images on this page are licensed under a
Creative Commons Attribution 2.5 India License. They may be freely used under the conditions of the license, with credit to
IndiaEVM.org.
http://indiaevm.org/media.html













